Understanding the Critical Role of a Risk Owner
It is essential in the present world where risk is more dynamic and global that the role of a risk owner is central to an organization’s security and compliance posture. Risk owners are supposed to be the primary stewards of specific risks and must be able to justify their assessment, management, and mitigation of the risks. One of the most crucial responsibilities of a risk owner is conducting thorough and effective risk reviews.
This guide is meant to help risk owners understand how to approach risk reviews so they can fulfill their responsibilities and support the organization’s risk management strategy.
General Obligations of a Risk Owner
This paper first outlines the general obligations of a risk owner before delving into the specifics of risk reviews.
1. Risk Accountability
In your position as a risk owner, you are responsible for:
- The correct identification of risks that are assigned to you
- Confirming that the right measures are taken
- Watching over the efficiency of risk management (control) measures
- Presenting risk information to the stakeholders who require it
2. Continuous Monitoring
Risk management is not an occasional process but an ongoing one:
- Of being watchful of events that may affect your risks
- Of recognizing potential risks before they become real risks
- Monitoring control effectiveness (control, in layman’s language)
- Observing the execution of risk treatment actions (control, which is being enhanced or created)
3. Cross-Functional Collaboration
For effective risk management, collaboration between different areas of the organization is necessary:
- Interacting with control owners to guarantee that the control is properly embedded in the organization
- Interfacing with infraops, desktop egineering, security, compliance, and business teams
- Interacting with senior management in the case of important risks
- Interacting with other risk owners in relation to related risks
4. Documentation and Reporting
This paper aims at emphasizing the importance of proper risk documentation:
- To ensure that risk descriptions are clear and specific
- Risk descriptions and justification of the assessment made (this doesn’t have to be a full analysis – sometimes, just a comment on the risk)
- Risk treatment plans and their implementation status
- The decisions made and the reasons for them
Preparing for a Risk Review: Essential Information to Consider
When you receive notification of an upcoming risk review, gathering relevant information is your first critical task. This preparation phase sets the foundation for an effective review.
The Risk Data Model: A Centralized View of Risk
The risk data model is a visual representation of the risk’s components and their relationships. It provides a centralized view of the risk, making it easier to understand and manage.
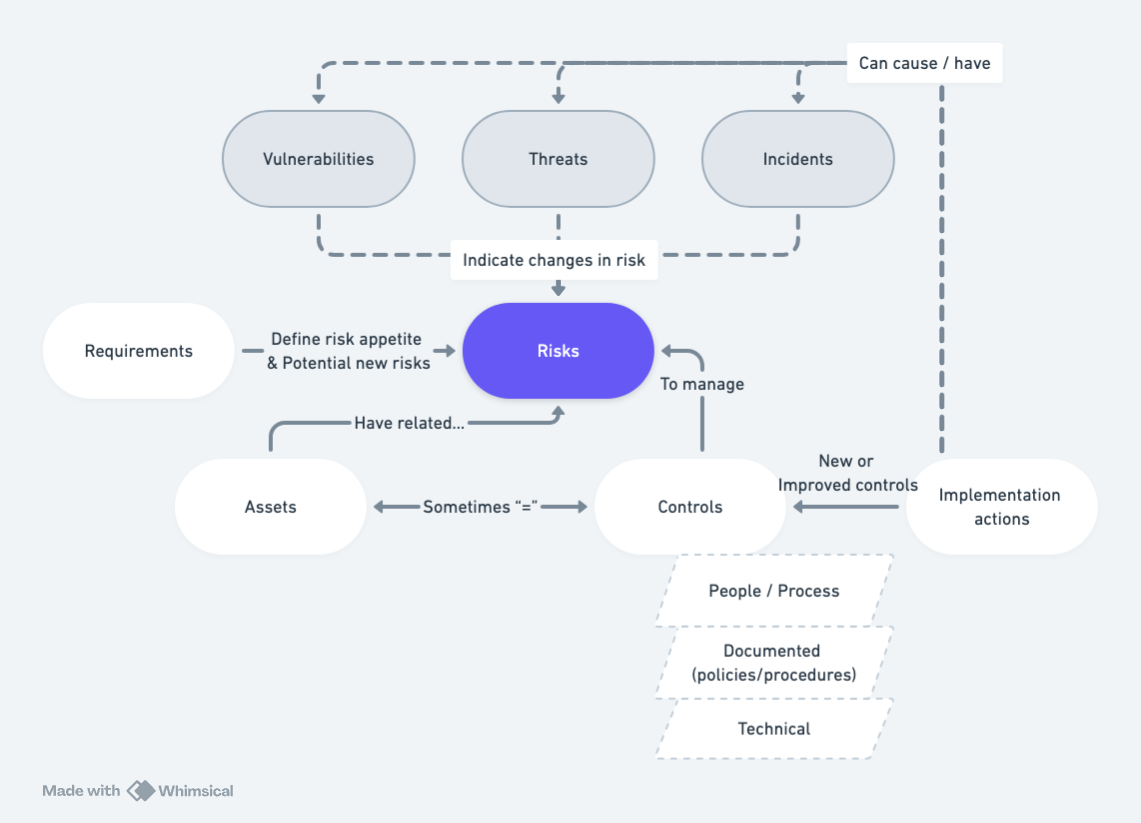
The risk data model includes the risk’s description, risk parameters (probability, impact, and overall rating), risk owner, related assets, controls, requirements, and treatment actions. It also includes other relevant information such as the risk’s history, including changes to the risk’s assessment, treatment plans, and their progress.
1. Related Events and Incidents
Compile information about events and incidents that have occurred since the last review:
- Security incidents related to your risk area
- Near-misses that could have resulted in risk materialization
- System outages or performance issues
- User complaints or feedback related to the risk area
2. Vulnerability Reports
Review recent vulnerability findings:
- New vulnerabilities identified in systems related to your risk
- Vulnerability scan results and their severity ratings
- Penetration testing findings
- Third-party security assessments
3. Threat Intelligence
Stay informed about evolving threats:
- Industry threat reports relevant to your risk domain
- Threat actor tactics, techniques, and procedures (TTPs)
- Changes in the threat landscape affecting your risk area
- Emerging threats that could impact your risk assessment
4. Organizational Changes
Consider how organizational changes might affect your risk:
- Changes in business processes or operations
- New systems or technologies implemented
- Modifications to existing systems
- Organizational restructuring
- Changes in third-party relationships or suppliers
- New regulatory requirements or compliance obligations
5. Control Effectiveness
Evaluate how existing controls have performed:
- Results of control testing or audits
- Control failures or deficiencies
- Changes to control implementation
- New controls implemented since the last review
Conducting the Risk Review: A Structured Approach
The risk review process itself should be methodical and comprehensive. Here’s a structured approach to ensure you cover all necessary aspects:
Risk Management Flow
The risk management process is a continuous cycle of identifying, assessing, prioritizing, and managing risks. The risk management flow diagram below illustrates the different stages of risk management and how they relate to the risk review process.
Some of the datapoints which can be used are similar to what is described here:
Try Interactive Risk Report Demo Here
1. Review and Update Risk Information
Start by reviewing the fundamental information about the risk:
Risk Description
- Is the risk description still accurate and comprehensive?
- Does it clearly articulate what could go wrong?
- Does it need to be updated based on new information or changes?
Linked Assets
- Are all relevant assets properly linked to the risk?
- Have new assets been introduced that should be linked?
- Should any assets be removed from the risk association?
Requirements and Controls
- Are all applicable requirements correctly linked?
- Are the controls associated with the risk still relevant?
- Should additional controls be linked based on new requirements?
Below is a sample screenshot from Peak Defence WINGMAN GRC on risk basic data:
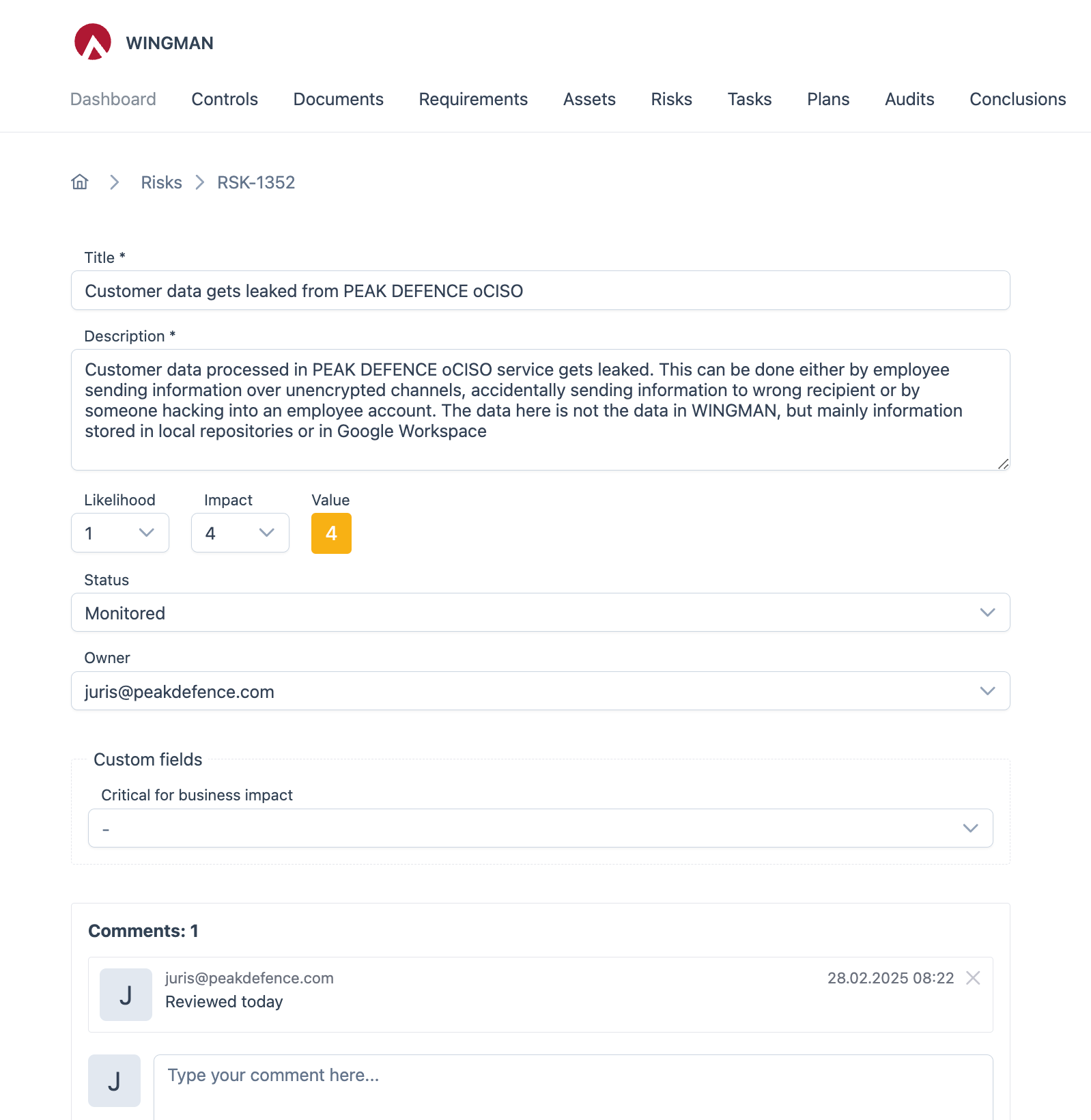
2. Reassess Risk Parameters
Next, evaluate whether the risk parameters need adjustment:
Probability Assessment
- Has the likelihood of the risk occurring changed?
- Have new threats emerged that affect probability?
- Have controls been implemented that reduce probability?
- Have there been incidents that suggest a higher probability?
Impact Assessment
- Has the potential impact of the risk changed?
- Have business changes affected the impact severity?
- Are there new impact dimensions to consider (financial, reputational, operational)?
- Have regulatory changes affected potential penalties or consequences?
Overall Risk Value
- Based on the updated probability and impact, has the overall risk value changed?
- Does the risk need to be escalated or de-escalated in priority?
- Is the risk within acceptable thresholds according to the organization’s risk appetite?
3. Document Your Assessment
Even if nothing has changed, documenting your review is crucial:
- Record the date of the review
- Note that all aspects were evaluated
- Confirm that the risk value remains the same
- Document your rationale for maintaining the current assessment
Evaluating Risk Treatment Actions
A critical component of the risk review is evaluating the status and effectiveness of risk treatment actions:
A sample screen from items linked to risk in Peak Defence WINGMAN GRC is below:
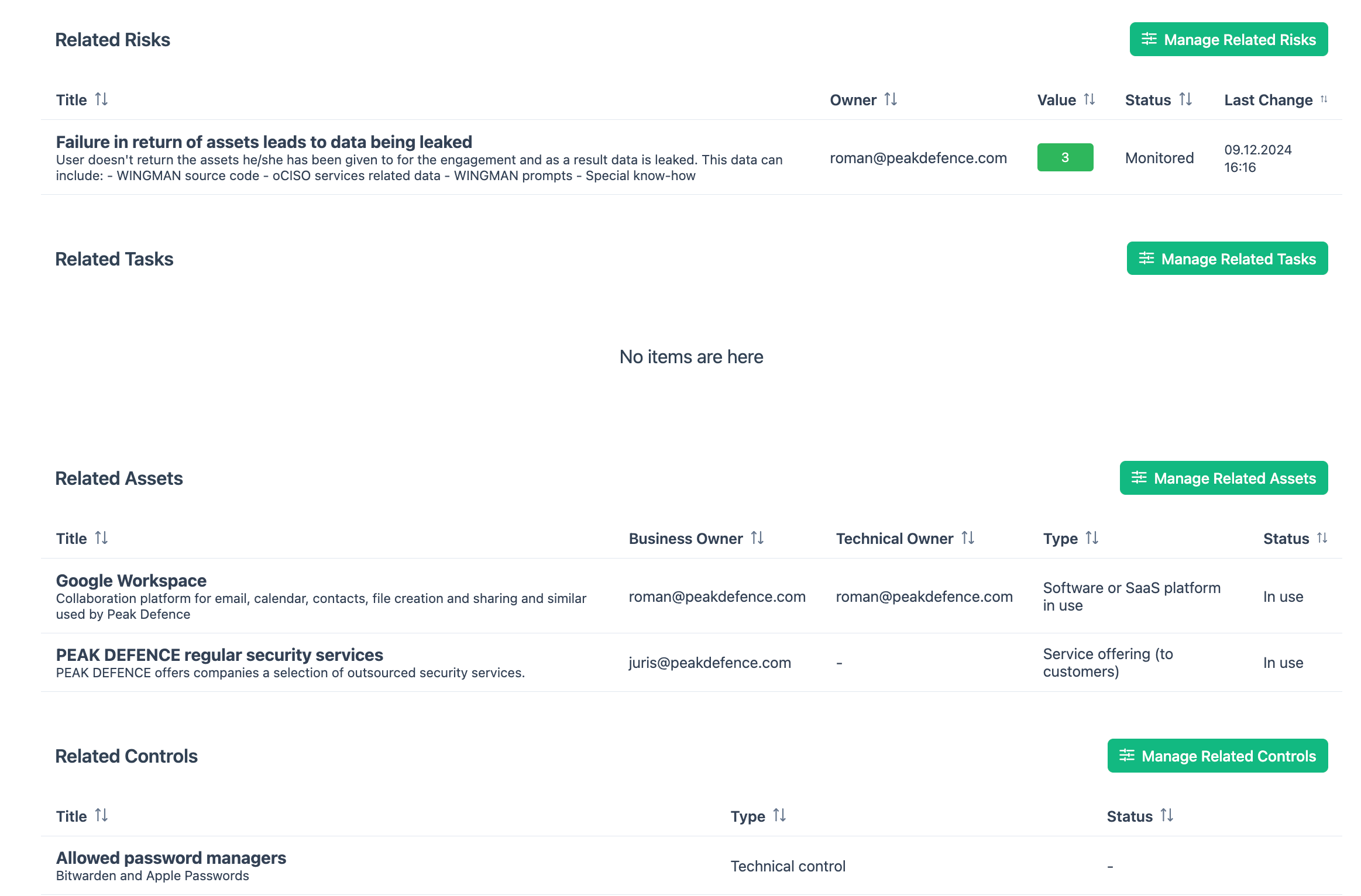
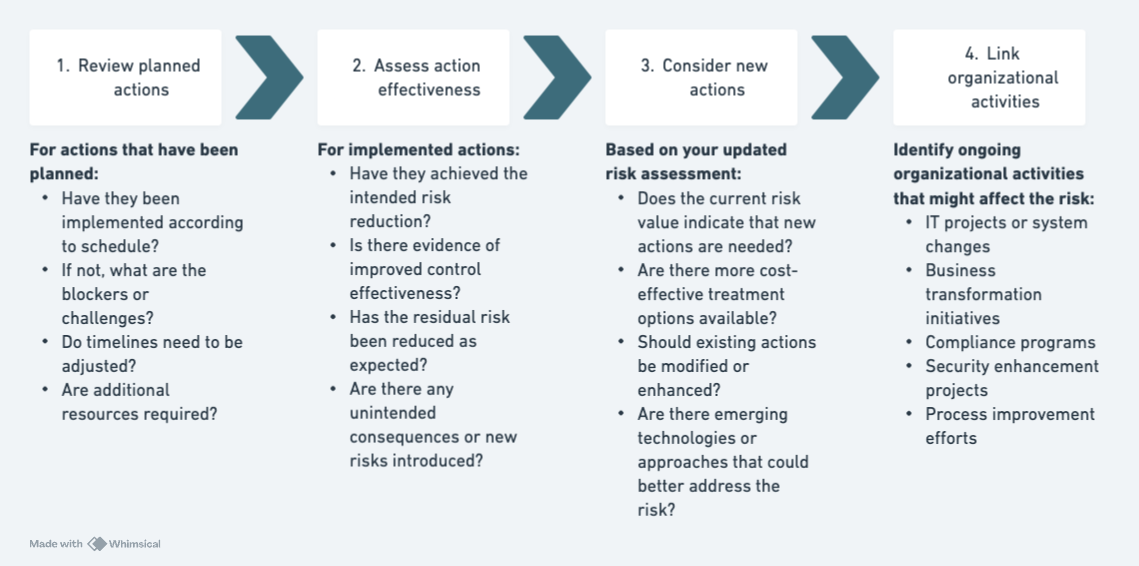
1. Review Planned Actions
For actions that have been planned:
- Have they been implemented according to schedule?
- If not, what are the blockers or challenges?
- Do timelines need to be adjusted?
- Are additional resources required?
2. Assess Action Effectiveness
For implemented actions:
- Have they achieved the intended risk reduction?
- Is there evidence of improved control effectiveness?
- Has the residual risk been reduced as expected?
- Are there any unintended consequences or new risks introduced?
3. Consider New Actions
Based on your updated risk assessment:
- Does the current risk value indicate that new actions are needed?
- Are there more cost-effective treatment options available?
- Should existing actions be modified or enhanced?
- Are there emerging technologies or approaches that could better address the risk?
4. Link Organizational Activities
Identify ongoing organizational activities that might affect the risk:
- IT projects or system changes
- Business transformation initiatives
- Compliance programs
- Security enhancement projects
- Process improvement efforts
For relevant activities:
- Link them to the risk in your documentation
- Assess how they might affect the risk (positively or negatively)
- Determine if the risk needs to be reevaluated based on these activities
- Coordinate with project teams to ensure risk considerations are addressed
Best Practices for Effective Risk Reviews
To maximize the value of your risk reviews, consider these best practices:
1. Maintain a Forward-Looking Perspective
While historical data is important, risk management is inherently forward-looking:
- Consider emerging trends and their potential impact
- Anticipate how planned organizational changes might affect the risk
- Look beyond immediate concerns to identify longer-term risk implications
- Consider various scenarios and their potential outcomes
2. Engage with Stakeholders
Risk reviews shouldn’t happen in isolation:
- Consult with subject matter experts for specialized insights
- Engage with business process owners to understand operational impacts
- Collaborate with control owners to assess control effectiveness
- Seek input from security, compliance, and IT teams
3. Challenge Assumptions
Effective risk reviews require critical thinking:
- Question whether previous assumptions still hold true
- Consider alternative perspectives on probability and impact
- Test the logic behind risk ratings
- Evaluate whether controls are truly effective or just appear to be
4. Document Comprehensively
Thorough documentation supports accountability and continuity:
- Record all significant findings and decisions
- Document the rationale behind risk assessments
- Maintain an audit trail of changes
- Ensure documentation is clear enough for others to understand
5. Follow Through
The risk review is not complete until actions are assigned and tracked:
- Ensure all agreed actions have clear owners
- Establish realistic timelines for implementation
- Set up regular check-ins on action progress
- Escalate delays or challenges promptly
Conclusion
As a risk owner, your role in conducting thorough risk reviews is fundamental to your organization’s risk management strategy. By systematically evaluating all aspects of your assigned risks—from the basic information to treatment actions—you contribute significantly to your organization’s resilience and security posture.
Remember that risk management is not a one-time activity but an ongoing process. Regular, structured risk reviews ensure that your organization maintains an accurate understanding of its risk landscape and can respond appropriately to changes and challenges.
By following the guidance outlined in this article, you’ll be well-equipped to fulfill your responsibilities as a risk owner and contribute to a more secure and resilient organization.